Intel has mounted a severe Reptar vulnerability in varied processors for desktops, servers, cell units and embedded techniques. This has additionally confirmed to be an issue for the newest Alder Lake, Raptor Lake, and Sapphire Rapids microarchitectures.
The Reptar vulnerability can be utilized to escalate privilegesacquire entry to delicate data, and trigger denial of service. Nonetheless, a minimum of its fixing doesn’t require intervention on the {hardware} degree, as was within the case of an LVI assault.
Reptar Vulnerability in Intel CPUs Permit for Privileges Escalation
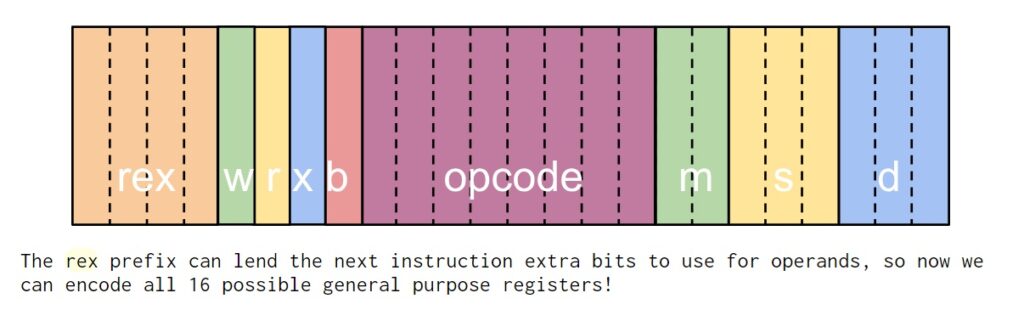
The vulnerability, found by Intel engineers themselves, has acquired the identifier CVE-2023-23583 and is described as an “REX prefix situation”.
Initially, it was believed that the error might be used solely to impress a denial of service. The vulnerability acquired solely a CVSS rating of 5.5. Intel initially deliberate to launch a patch for it in March 2024.
Nonetheless, deeper evaluation confirmed that there was a solution to exploit the bug to escalate privileges. And Intel moved the discharge date of the patch to November 2023. In consequence, the vulnerability ranking was modified to eight.8 factors on the CVSS scale.
Beneath sure circumstances, uncommon circumstances have been recognized on Intel microarchitectures. Executing an instruction (REP MOVSB) encoded with a redundant REX prefix could end in unpredictable system conduct. And likewise trigger a crucial crash or freeze. And in some situations – to extend privileges from CPL3 to CPL0.Intel engineers report.
Intel doesn’t anticipate any non-malware software program to come across this drawback in the actual world. It’s anticipated that redundant REX prefixes is not going to be current within the code and won’t be generated by compilers.
Malicious exploitation of the Reptar situation requires the execution of arbitrary code. Additionally, as part of an inner evaluate Intel recognized the potential for privilege escalation in sure situations.
Methods with affected processors, together with Alder Lake, Raptor Lake and Sapphire Rapids, have already acquired up to date firmwareand these patches don’t impression efficiency.
Different Threats to Intel Processors
The historical past of Home windows processor issues is sort of wealthy. We additionally wrote in regards to the Snoop assault, which may cease processors. And in regards to the Platypus assault, which might be utilized by attackers to steal information. And likewise about issues with Lively Administration Expertise (AMT) and Intel Normal Manageability (ISM).
Nonetheless, earlier this 12 months the media additionally wrote about some of the severe errors within the historical past of Intel processors. It was CVE-2021-39296 situation (10 out of 10 on the CVSS scale). This vulnerability affected the built-in BMC (Baseboard Administration Controller) and OpenBMC firmware on a number of of the corporate’s platforms. The problem CVE-2021-39296, as its ID exhibits, was found again in 2021, however was mounted solely two years later.
Are processor vulnerabilities that harmful?
Issues with processors are normally perceived as painful as a consequence of the truth that they’re all over the place. They’re the premise of virtually any digital gadget. And an exploitable vulnerability in Intel or AMD merchandise could make thousands and thousands of customers all over the world depending on the actions of attackers.
An entire record of Intel processors affected by the CVE-2023-23583 vulnerability, in addition to suggestions for resolving it, can be found right here.